From Smartphones to Strategic Infrastructure: What MWC Reveals About the New Connectivity Battlespace
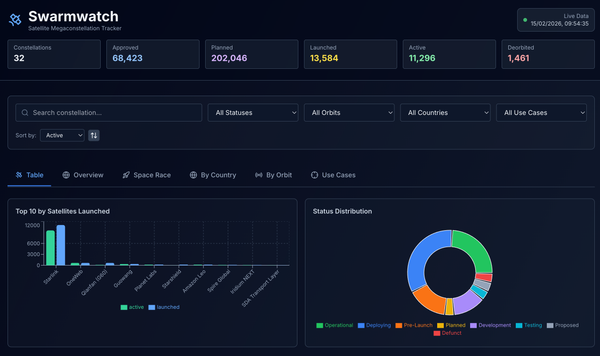
Mobile World Congress 2026 kicked off this week, and walking the halls on the first day, it was clear that a pattern had quickly emerged. Satellite connectivity is no longer being marketed as a niche solution for remote villages or maritime users. It is being embedded into the core architecture